Advanced Internet Access Techniques
In some countries, it’s prohibited to rot your brain on Instagram Reels. Fortunately, that’s a solvable problem.
There are plenty of solutions for bypassing censorship. My current setup is based on Xray-core and I will be sharing the approaches and ideas behind it. All configurations are available in this repo.
As of writing this, the latest xray version is v26.2.6 and my setup is confirmed working, but that obviously doesn’t guarantee the same behavior in the future.
The setup
My current setup involves several solutions combined. I have one server beyond the firewall and another that I’m renting behind it. I’m also using a CDN which does not block domain fronting (yet) and a load balancer which allows getting a clean IP.
The core idea is to combine 3 different protocols on the final layer to always have something to fall back to.
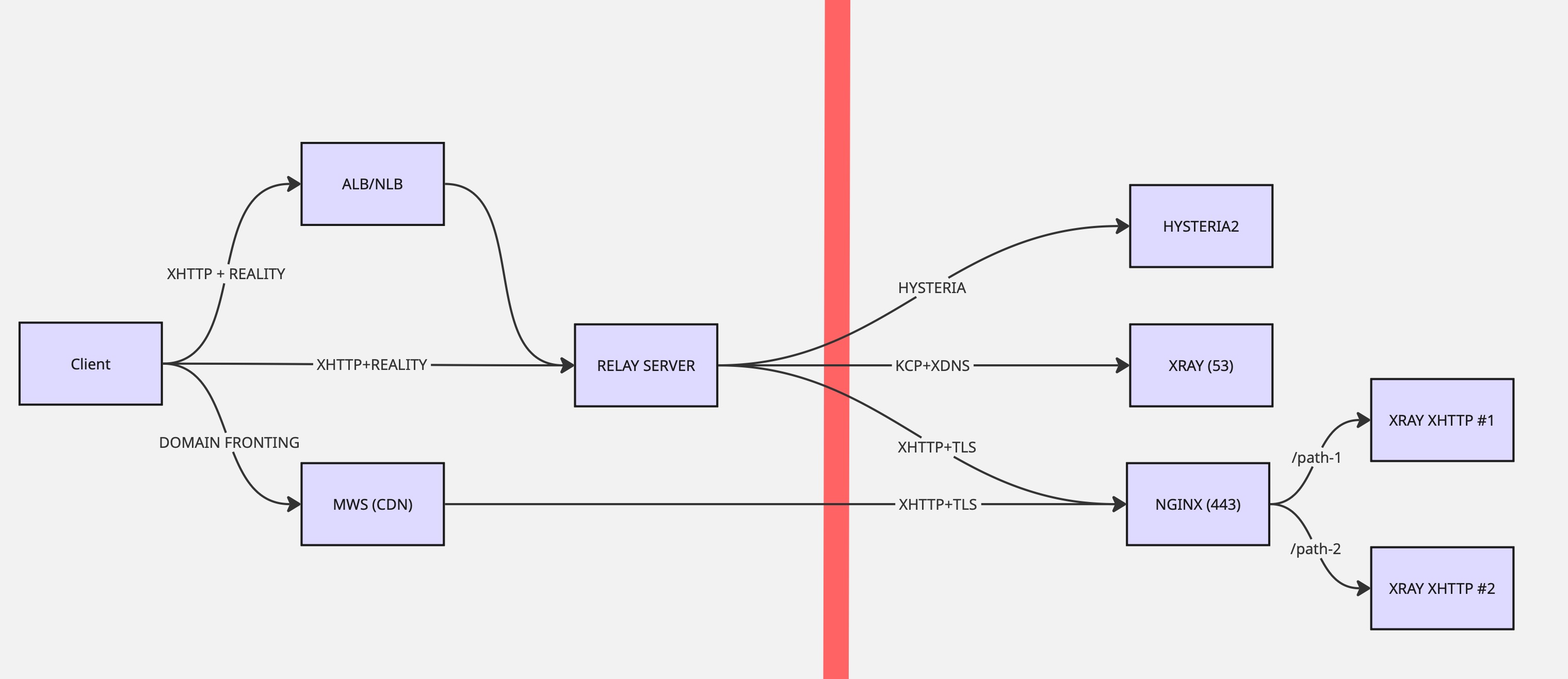
Freedom server
I have 3 IP addresses on one VPS — two of them for XHTTP split transmission (uploads on one IP, downloads on another) and the third for hysteria only.
For the XHTTP setup, there is a steal from oneself strategy — a “real” website hosted by nginx, which proxies matching requests to underlying xray XHTTP inbounds listening on different unix sockets. I have two different XHTTP inbounds, which essentially allows creating N XHTTP inbounds on different nginx paths — each with different XHTTP stream settings — cookie placements, padding keys, upload methods, obfuscation modes, and so on. This gives a huge amount of possible combinations on the same VPS, differentiated only by the path parameter.
I’m also running a standalone hysteria server listening on its dedicated IP address on port 443, which allows running both nginx and hysteria on the same VPS since they’re bound to different addresses.
As a fallback I’m running KCP + XDNS, which allows sending traffic using DNS queries — the last resort for when everything else is blocked.
Relay server
Currently, there are whitelists on mobile internet that only allow connecting to whitelisted domains and IP addresses — this varies by region and time but the whole idea is based on this. To bypass it, there are several approaches:
- Relay server — acts as a middleman for the connection to the freedom server. The client first connects to the server behind the firewall, which then connects to the freedom server on its behalf.
- ALB/NLB — forwards the traffic to the relay server, giving you a clean IP that you can rotate whenever the current one gets blocked. An ALB operates at layer 7 (HTTP) and can inspect headers, terminate TLS, and route by path — useful when the relay speaks XHTTP. An NLB operates at layer 4 (TCP/UDP) and just forwards raw connections with lower latency, which works for any protocol. Both achieve the same goal of providing a rotatable frontend IP.
- CDN domain fronting — using a CDN that allows domain fronting (MWS, at the time of writing). Client requests are first sent to the CDN, which then forwards them to the freedom server.
Transparent proxy
I’m running xray on my Unifi router (which is Linux based) in tproxy mode — any device on my WiFi gets transparently proxied through xray with no per-device configuration.
The router runs DoH resolvers for Google and Cloudflare, and the freedom server runs systemd-resolved for its own DNS. Here’s what happens when a device on the network makes a request:
- The device resolves the domain through the router’s DoH — one encrypted DNS query, invisible to the firewall
- The device opens a connection to the resolved IP — iptables tproxy rules intercept it and hand it to xray’s
dokodemo-doorinbound - Xray sniffs the TLS handshake to extract the domain from SNI
- With
routeOnly: true, the sniffed domain is used only for routing decisions — the destination stays as the original resolved IP - With
domainStrategy: "AsIs", xray skips any DNS resolution of its own — it matches the sniffed domain against domain rules (ad blocking) and the original IP against geoip rules (traffic splitting)
The result is traffic splitting with a single DNS query per connection and zero additional resolution by xray. The geoip:google and geoip:cloudflare routing rules also ensure that any direct DNS queries from devices (say, plaintext UDP to 8.8.8.8) get proxied rather than leaking in the clear.
This combination matters — routeOnly: true is what makes the whole approach work. With routeOnly: false, xray replaces the destination with the sniffed domain and throws away the original IP. At that point geoip:ru rule has nothing to match against — there’s no IP anymore, just a domain. And since domainStrategy: "AsIs" tells xray not to resolve anything, all IP-based splitting silently stops and everything falls through to the catch-all proxy rule. To get splitting back you’d need IPIfNonMatch or IPOnDemand, which means xray resolves DNS on every connection — defeating the whole point. So routeOnly: true + AsIs is the only combination that gives you both domain and IP routing with zero DNS overhead from xray.
The tradeoff is splitting accuracy. Since all DNS goes through foreign resolvers (Google and Cloudflare), domestic sites that use local CDNs can resolve to IPs outside the geoip:ru range — the CDN returns edge nodes closest to the resolver, not to the client. These connections get routed through the proxy instead of going direct, which breaks sites that expect local access. For the vast majority of traffic the split is correct though, and the setup is effectively zero-maintenance.
Configs
Below are the configuration files for each component. Sensitive values are left empty — fill in your own IPs, domains, UUIDs, and keys.
nginx.conf
Nginx terminates TLS for all XHTTP traffic. It listens on two different IP addresses (for two separate domains and certificates) and proxies matching paths to xray unix sockets. Everything else is served as a static site — the steal from oneself strategy.
server {
listen [::]:80 default_server ipv6only=off;
server_name _;
return 301 https://$host$request_uri;
}
server {
http2 on;
http3 on;
listen ip-1:443 ssl reuseport so_keepalive=on ipv6only=off;
listen ip-1:443 quic reuseport ipv6only=off;
# The CNAME domain + direct domain to point as CDN source
server_name cdn.domain.com direct.domain.com;
index index.html;
root /etc/nginx/www;
ssl_certificate /etc/nginx/ssl/domain.com.crt;
ssl_certificate_key /etc/nginx/ssl/domain.com.key;
ssl_protocols TLSv1.2 TLSv1.3;
client_header_timeout 30m;
keepalive_timeout 30m;
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains; preload" always;
add_header X-Frame-Options DENY;
add_header X-Content-Type-Options nosniff;
location /path-1/ {
client_max_body_size 0;
client_body_timeout 30m;
grpc_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
grpc_read_timeout 30m;
grpc_send_timeout 30m;
grpc_pass unix:/dev/shm/xhttp-default.socket;
}
location /path-2/ {
client_max_body_size 0;
client_body_timeout 30m;
grpc_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
grpc_read_timeout 30m;
grpc_send_timeout 30m;
grpc_pass unix:/dev/shm/xhttp-stealth.socket;
}
location / {
try_files $uri $uri/ =404;
}
}
server {
http2 on;
http3 on;
listen ip-2:443 ssl;
listen ip-2:443 quic;
server_name domain-2;
index index.html;
root /etc/nginx/www;
ssl_certificate /etc/nginx/ssl/domain-2.crt;
ssl_certificate_key /etc/nginx/ssl/domain-2.key;
ssl_protocols TLSv1.2 TLSv1.3;
client_header_timeout 30m;
keepalive_timeout 30m;
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains; preload" always;
add_header X-Frame-Options DENY;
add_header X-Content-Type-Options nosniff;
location /path-1/ {
client_max_body_size 0;
client_body_timeout 30m;
grpc_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
grpc_read_timeout 30m;
grpc_send_timeout 30m;
grpc_pass unix:/dev/shm/xhttp-default.socket;
}
location /path-2/ {
client_max_body_size 0;
client_body_timeout 30m;
grpc_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
grpc_read_timeout 30m;
grpc_send_timeout 30m;
grpc_pass unix:/dev/shm/xhttp-stealth.socket;
}
location / {
try_files $uri $uri/ =404;
}
}freedom.jsonc
The freedom server runs xray with two XHTTP inbounds on unix sockets — one default and one with stealth customizations (custom cookie placements, padding, and upload methods) — plus a KCP+XDNS inbound for DNS-based transport on a separate IP.
{
"log": {
"error": "/var/log/remnanode/access.log",
"access": "/var/log/remnanode/access.log",
"loglevel": "none"
},
"inbounds": [
{
"tag": "XHTTP-DEFAULT",
"listen": "/dev/shm/xhttp-default.socket,0666",
"protocol": "vless",
"settings": {
"clients": [],
"decryption": "none"
},
"sniffing": {
"enabled": true,
"routeOnly": false,
"destOverride": [
"http",
"quic",
"tls"
]
},
"streamSettings": {
"network": "xhttp",
"xhttpSettings": {
"path": "/path-1"
}
}
},
{
"tag": "XHTTP-STEALTH",
"listen": "/dev/shm/xhttp-stealth.socket,0666",
"protocol": "vless",
"settings": {
"clients": [],
"decryption": "none"
},
"sniffing": {
"enabled": true,
"routeOnly": false,
"destOverride": [
"http",
"quic",
"tls"
]
},
"streamSettings": {
"network": "xhttp",
"xhttpSettings": {
"path": "/path-2",
"seqKey": "rid",
"sessionKey": "sid",
"xPaddingKey": "t",
"seqPlacement": "cookie",
"xPaddingHeader": "X-Trace-Id",
"xPaddingMethod": "tokenish",
"sessionPlacement": "cookie",
"uplinkHTTPMethod": "PUT",
"xPaddingObfsMode": true,
"xPaddingPlacement": "cookie"
}
}
},
{
"tag": "XDNS",
"port": 53,
"listen": "ip", // do not set to 0.0.0.0 or it will conflict with the stub listener
"protocol": "vless",
"settings": {
"clients": [
{
"id": ""
}
],
"decryption": "none"
},
"streamSettings": {
"network": "kcp",
"kcpSettings": {
"mtu": 900
},
"finalmask": {
"udp": [
{
"type": "xdns",
"settings": {
"domain": "" // The NS record domain
}
}
]
}
}
}
],
"outbounds": [
{
"tag": "direct",
"protocol": "freedom"
},
{
"tag": "warp",
"protocol": "socks",
"settings": {
"port": 45643,
"address": "127.0.0.1"
}
},
{
"tag": "block",
"protocol": "blackhole"
}
],
"routing": {
"rules": [
{
"ip": [
"geoip:private",
"geoip:ru"
],
"outboundTag": "block"
},
{
"user": [
"22"
],
"outboundTag": "warp"
}
]
}
}relay.jsonc
The relay server accepts XHTTP+REALITY connections from clients behind the firewall and forwards them to the freedom server. In production, its outbounds mirror the client config — the config below is simplified to show the inbound structure only.
{
"log": {
"loglevel": "none"
},
"inbounds": [
{
"tag": "RELAY-XHTTP",
"port": 443,
"protocol": "vless",
"settings": {
"clients": [],
"decryption": "none"
},
"streamSettings": {
"network": "xhttp",
"security": "reality",
"realitySettings": {
"target": "",
"shortIds": [
""
],
"privateKey": "",
"serverNames": [
""
]
}
}
}
],
"outbounds": [
// Same as the client outbounds but with the extra RELAY-XHTTP inbound
{
"tag": "direct",
"protocol": "freedom"
},
{
"tag": "block",
"protocol": "blackhole"
}
]
}client.jsonc
The client ties everything together. burstObservatory health-checks the primary outbounds, a leastLoad balancer picks the best available one with xdns as the ultimate fallback, and routing rules handle traffic splitting and ad blocking. The tproxy dokodemo-door inbound enables transparent proxying for the entire network.
{
"log": {
"loglevel": "none"
},
"burstObservatory": {
"subjectSelector": [
"freedom-direct",
"freedom-direct-stealth",
"freedom-mts-stealth",
"hysteria"
],
"pingConfig": {
"destination": "https://connectivitycheck.gstatic.com/generate_204",
"connectivity": "http://connectivitycheck.platform.hicloud.com/generate_204",
"interval": "1m",
"sampling": 3,
"timeout": "2s"
}
},
"routing": {
"balancers": [
{
"tag": "best-proxy-balancer",
"selector": [
"freedom-direct",
"freedom-direct-stealth",
"freedom-mts-stealth",
"hysteria"
],
"fallbackTag": "xdns",
"strategy": {
"type": "leastLoad"
}
}
],
"rules": [
{
"domain": [
"geosite:category-ads-all"
],
"outboundTag": "block"
},
{
"ip": [
"geoip:cloudflare",
"geoip:google"
],
"balancerTag": "best-proxy-balancer" // Make sure all DNS queries are proxied
},
{
"ip": [
"geoip:ru"
],
"outboundTag": "direct" // Traffic splitting
},
{
"network": "tcp,udp",
"balancerTag": "best-proxy-balancer"
}
]
},
"inbounds": [
{
"tag": "socks",
"listen": "127.0.0.1",
"port": 10808,
"protocol": "socks",
"settings": {
"auth": "none",
"udp": true
}
},
{
"tag": "transparent",
"port": 12345,
"listen": "0.0.0.0",
"protocol": "dokodemo-door",
"settings": {
"network": "tcp,udp",
"followRedirect": true
},
"sniffing": {
"enabled": true,
"destOverride": [
"http",
"tls",
"quic"
],
"routeOnly": true
},
"streamSettings": {
"sockopt": {
"tproxy": "tproxy"
}
}
}
],
"outbounds": [
{
"tag": "alb-relay", // Not in the balancer — add to selector when direct paths are blocked
"protocol": "vless",
"settings": {
"vnext": [
{
"address": "", // IP address of the ALB relay server
"port": 443,
"users": [
{
"id": "",
"flow": "",
"encryption": "none"
}
]
}
]
},
"streamSettings": {
"network": "xhttp",
"security": "reality",
"realitySettings": {
"serverName": "",
"publicKey": ""
}
}
},
{
"tag": "hysteria",
"protocol": "hysteria",
"settings": {
"version": 2,
"address": "", // Hysteria server name
"port": 443
},
"streamSettings": {
"network": "hysteria",
"hysteriaSettings": {
"version": 2,
"auth": "" // Hysteria password
},
"security": "tls",
"tlsSettings": {
"serverName": "" // Hysteria server name
},
"finalmask": {
"udp": [
{
"type": "salamander",
"settings": {
"password": ""
}
}
]
}
}
},
{
"tag": "xdns",
"protocol": "vless",
"settings": {
"vnext": [
{
"address": "", // Domain pointing to the DNS server IP
"port": 53,
"users": [
{
"id": "",
"encryption": "none"
}
]
}
]
},
"streamSettings": {
"network": "kcp",
"kcpSettings": {
"mtu": 130
},
"finalmask": {
"udp": [
{
"type": "xdns",
"settings": {
"domain": "" // DNS server NS record
}
}
]
}
}
},
{
"tag": "freedom-direct",
"protocol": "vless",
"settings": {
"vnext": [
{
"address": "", // Freedom server IP or domain
"port": 443,
"users": [
{
"id": "",
"flow": "",
"encryption": "none"
}
]
}
]
},
"streamSettings": {
"network": "xhttp",
"xhttpSettings": {
"path": "/path-1",
"extra": {
"xmux": {
"maxConnections": "4-8",
"cMaxReuseTimes": "64-128",
"hMaxRequestTimes": "600-900",
"hMaxReusableSecs": "1800-2700",
"hKeepAlivePeriod": 30
},
"downloadSettings": { // Traffic splitting
"address": "",
"port": 443,
"network": "xhttp",
"security": "tls",
"tlsSettings": {
"alpn": [
"h3" // Force QUIC for downloads
]
},
"xhttpSettings": {
"host": "",
"path": "/path-1",
"extra": {
"xmux": {
"maxConnections": "4-8",
"cMaxReuseTimes": "64-128",
"hMaxRequestTimes": "600-900",
"hMaxReusableSecs": "1800-2700",
"hKeepAlivePeriod": 30
}
}
}
}
}
},
"security": "tls"
}
},
{
"tag": "freedom-direct-stealth",
"protocol": "vless",
"settings": {
"vnext": [
{
"address": "",
"port": 443,
"users": [
{
"id": "",
"flow": "",
"encryption": "none"
}
]
}
]
},
"streamSettings": {
"network": "xhttp",
"xhttpSettings": {
"path": "/path-2",
"seqKey": "rid",
"mode": "stream-one", // Traffic splitting and custom xmux not yet supported in this mode
"sessionKey": "sid",
"xPaddingKey": "t",
"seqPlacement": "cookie",
"xPaddingHeader": "X-Trace-Id",
"xPaddingMethod": "tokenish",
"sessionPlacement": "cookie",
"uplinkHTTPMethod": "PUT",
"xPaddingObfsMode": true,
"xPaddingPlacement": "cookie"
},
"security": "tls",
"tlsSettings": {
"alpn": [
"h3",
"h2"
]
}
}
},
{
"tag": "freedom-mts-stealth",
"protocol": "vless",
"settings": {
"vnext": [
{
"address": "", // Domain to front
"port": 443,
"users": [
{
"id": "",
"flow": "",
"encryption": "none"
}
]
}
]
},
"streamSettings": {
"network": "xhttp",
"xhttpSettings": {
"host": "", // Your domain with CNAME to the CDN technical domain
"path": "/path-2",
"seqKey": "rid",
"sessionKey": "sid",
"xPaddingKey": "t",
"seqPlacement": "cookie",
"xPaddingHeader": "X-Trace-Id",
"xPaddingMethod": "tokenish",
"sessionPlacement": "cookie",
"uplinkHTTPMethod": "PUT",
"xPaddingObfsMode": true,
"xPaddingPlacement": "cookie"
},
"security": "tls",
"tlsSettings": {
"alpn": [
"h3",
"h2"
]
}
}
},
{
"tag": "direct",
"protocol": "freedom"
},
{
"tag": "block",
"protocol": "blackhole"
}
]
}